The protection wall is one of the most important safety features in the computer environment.
In the classic sense, the protection wall is prepared on a device, such as a computer that meets one tightly specific task – those in companies, public authorities and scientific institutions, for example. The wall protection wall monitors the relationship between two networks, such as the internal local network and the Internet, to prevent unauthorized access.
There are also personal protection walls such as those that were previously composed in Windows, or available as a free solution or a paid software.
Unlike the classic wall of protection, the PC Wall does not protect a complete network, but only the individual computer that is installed on it. It is the barrier that prevents any harmful elements from accessing the files that you have stored locally.
Windows Wall
Microsoft calls Windows Wall built -in Windows Defender. This is the most important thing to know about the defender protection wall:
Since the formation of the protection wall is complicated and requires a lot of previous knowledge of the user, Microsoft has set three standard configurations for the defender’s protection wall.
Which of these is activated depends on the specified network profile.
If you select the general identification file in Windows settings within the “Network and the Internet”, Windows stops the computer from the outside world. In this case, the computer cannot be found on the network and files and printers cannot be shared with other users.
If you are not connected to a field, you can choose between a network profile in Windows, “PUBLIC” and “Private”. If you select “General”, Windows greatly closes the doors.
Chris Hoffman / IDG
However, if you set the profile, you can share folders, files and printers with others and use applications for internal communication.
Windows also provides a field profile for professional networks.
Windows Wall in practice
The Windows Wall is active immediately after installing the operating system and analyzing all the data packages received to determine whether it has been requested by anyone.
This is called government packages inspection (SPI), and therefore the Windows Wall is a packet protection wall.
However, software like Facebook Messenger or remote maintenance tools like TeamvieWer will not work if they cannot receive unwanted messages or calls. When installed behind the wall of the protection, they open one or more outlets from which they receive messages.
It is also customizing other protection wall settings. Re -modification by the user is not necessary.
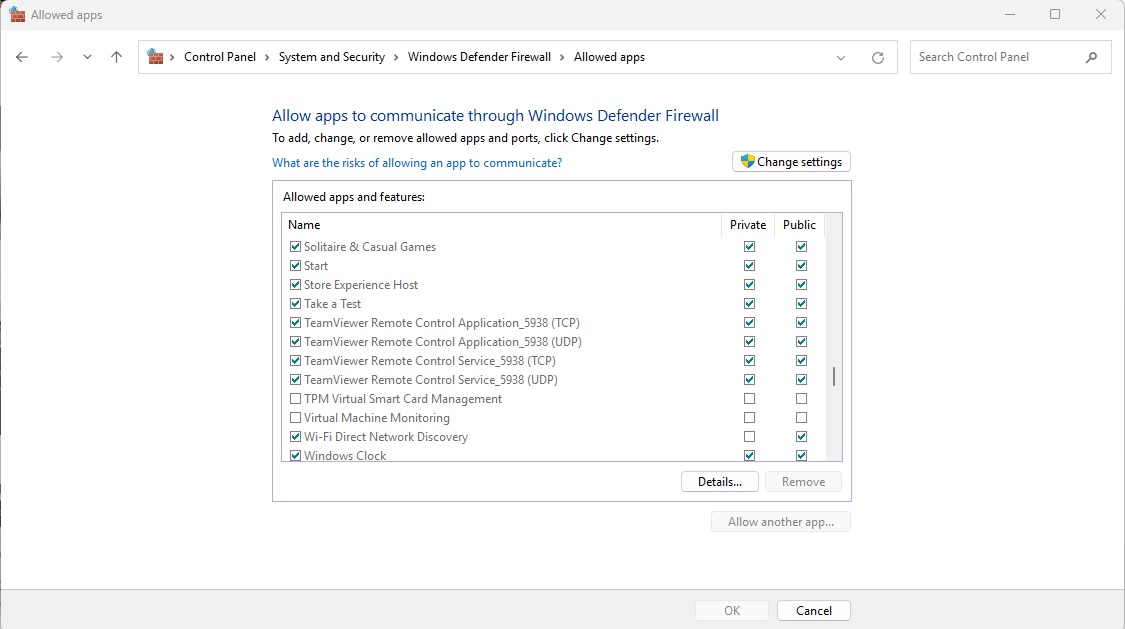
TeamvieWer and other applications that interact with signals from the outside set the Windows Wall to the Windows Wall according to this during installation.
foundry
Judgment of the defender protection wall
The Windows Wall protects the computer from harmful programs that infiltrate another computer and now wants to spread over the network. Therefore, it is highly recommended not to cancel its activation.
However, at least in the default setting, he cannot prevent harmful programs that have been able to infect one computer from trying to spread it to other computers. Specialized Wall Applications can do this better.
Walls for protection from third -party manufacturers
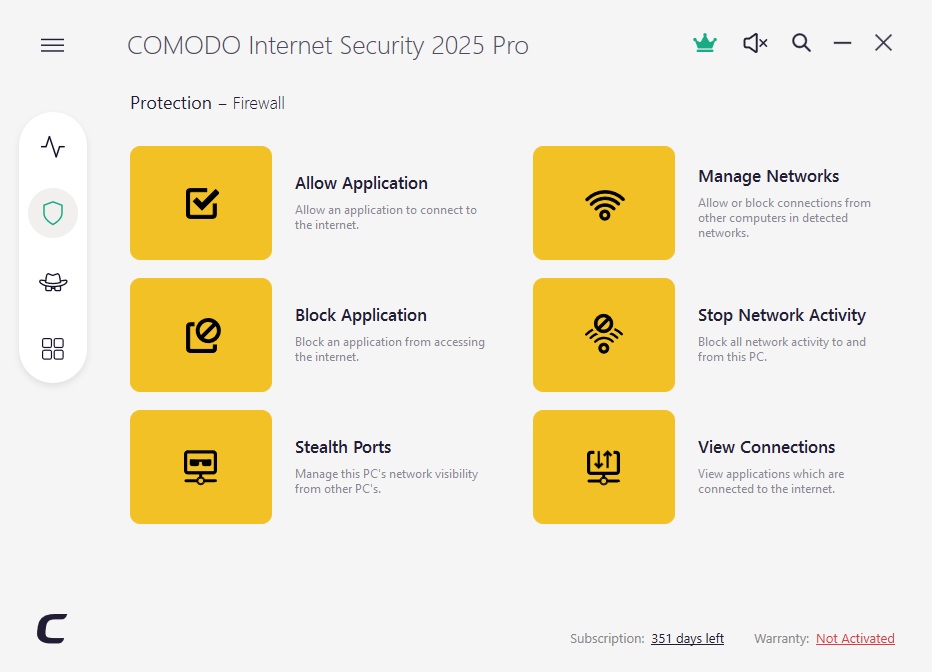
The Comodo protection wall can block applications and hide the computer in the network, and the list of programs currently connected to the Internet. However, it only comes in a full package with the anti -virus program.
Comodo
If you are traveling a lot and using your notebook to connect to LAN and WLAN networks for other people, you will not be able to control naturally on the router settings.
In this case, we recommend using a third party protection wall. The Comodo Wall, which is sold as part of the Comodo Internet Security package, is widely used. Unfortunately, the package can only be installed as a whole, and the setting also includes the comodo antivirus program.
Once the installation is complete, click the “Protection” shield icon on the left side and click on the “Wall of the Protection” in the next window.
You can then prohibit or allow applications to connect to the Internet, you can block the connections received via the ports blocks or report them, you can manage network connections and active connections to the Internet.
If you are a traveler and in a foreign wlan, for example, it is advised to hide the ports and only allow the applications you already need.
In some cases, you may need to allow several programs for programs to access the Internet. You can often find information about this from the manufacturer or on online help forums.
Mobile computers require a more comprehensive protection function than fixed computers. It is recommended to create a more composition and feature of a third -party manufacturer.
Sand box for isolation
Sand boxes are composed of personal protection walls. Under “protection”, you can access the Comodo sand function, which is called “containment” here. The sand box is used to run the individual applications specified in a closed memory area where no damage to the rest of the computer can be caused.
In the sand box, for example, suspicious downloads and other programs can be implemented without the user worrying about hunting the virus.
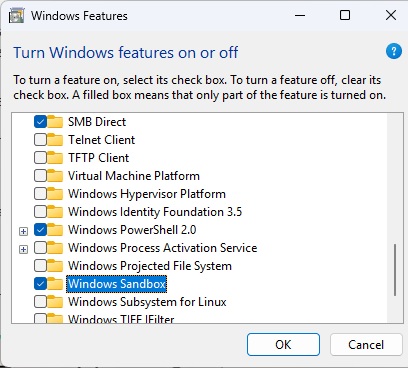
The Windows Sandbox box must be activated via “software and features” in the control panel.
foundry
Windows Pro also has a sand box, but you should activate it first. (Not available for Windows Home.) To do this, open the control panel and move to “software and features” in the icon display. In the next window, click “Enabling or disables Windows features”, then scroll down, and customize the box next to “Windows Sandbox”.
After confirming with “OK”, Windows installs some files and then restart. After logging in, you will see a window with the second Windows desktop. To test the programs there, you can copy it to the sand box using the portfolio.
You can close the sand box window like any other window. To open it again, enter Windows sand box In the search field in the taskbar and press Enter.
More reading: Be safe! How did you prepare a “mad computers madly” with a Windows sand box to browse the risky web
Vocational protection wall for home use
Professional protection walls usually work on devices, that is, their own devices, and thus cost several thousand dollars.
However, there is a cheaper option: free IPFIRE IPFire is available for Raspberry PI 4B with 1GB RAM and more.
The program can protect the entire networks from the outside world, easy to use, and even provides an optional infiltration system (IDS) that monitors the changes caused by malware. With identifiers, however, memory expansion should be 4 GB or more.
This article was originally appeared in our sister’s publication PC-Welt It was translated and translated from German.
adxpro.online
